Introduction
Navigating the complexities of automation in security policies is no small feat for organizations striving to enhance their operational efficiency. As businesses increasingly turn to technologies like Robotic Process Automation (RPA) to streamline workflows, they encounter a range of challenges—from integrating automated systems with existing frameworks to overcoming employee resistance rooted in fear and misunderstanding.
However, by adopting strategic training and communication practices, organizations can effectively demonstrate the transformative benefits of automation. This article delves into the critical aspects of automation, including:
- The importance of golden configuration validation for compliance
- Strategies to overcome resistance
- Metrics to measure success
By addressing these key areas, organizations can unlock the full potential of automation, driving innovation and operational excellence.
Identifying Key Automation Challenges in Security Policies
The challenges of automation in security policies present an automation challenge that entities must navigate for effective implementation. The automation challenges include:
- Integrating automated systems with existing security frameworks
- Ensuring continuous monitoring
- Keeping security protocols updated in line with evolving threats
Moreover, companies may encounter an automation challenge from staff familiar with manual methods who might be reluctant to rely on automated systems.
To tackle the automation challenges, it is crucial for organizations to participate in comprehensive training and communication strategies that highlight the advantages of mechanized processes, such as improved efficiency and minimized errors through Robotic Process Automation (RPA). Additionally, RPA can play a crucial role in addressing talent retention issues by alleviating the burden of repetitive tasks, allowing employees to focus on more strategic initiatives.
Establishing clear protocols to address the automation challenge of security tasks not only streamlines operations but also aligns with regulatory standards, thereby empowering teams to focus on more strategic, value-adding work while modernizing outdated systems.
Ensuring Compliance: The Importance of Golden Configuration Validation in Automation
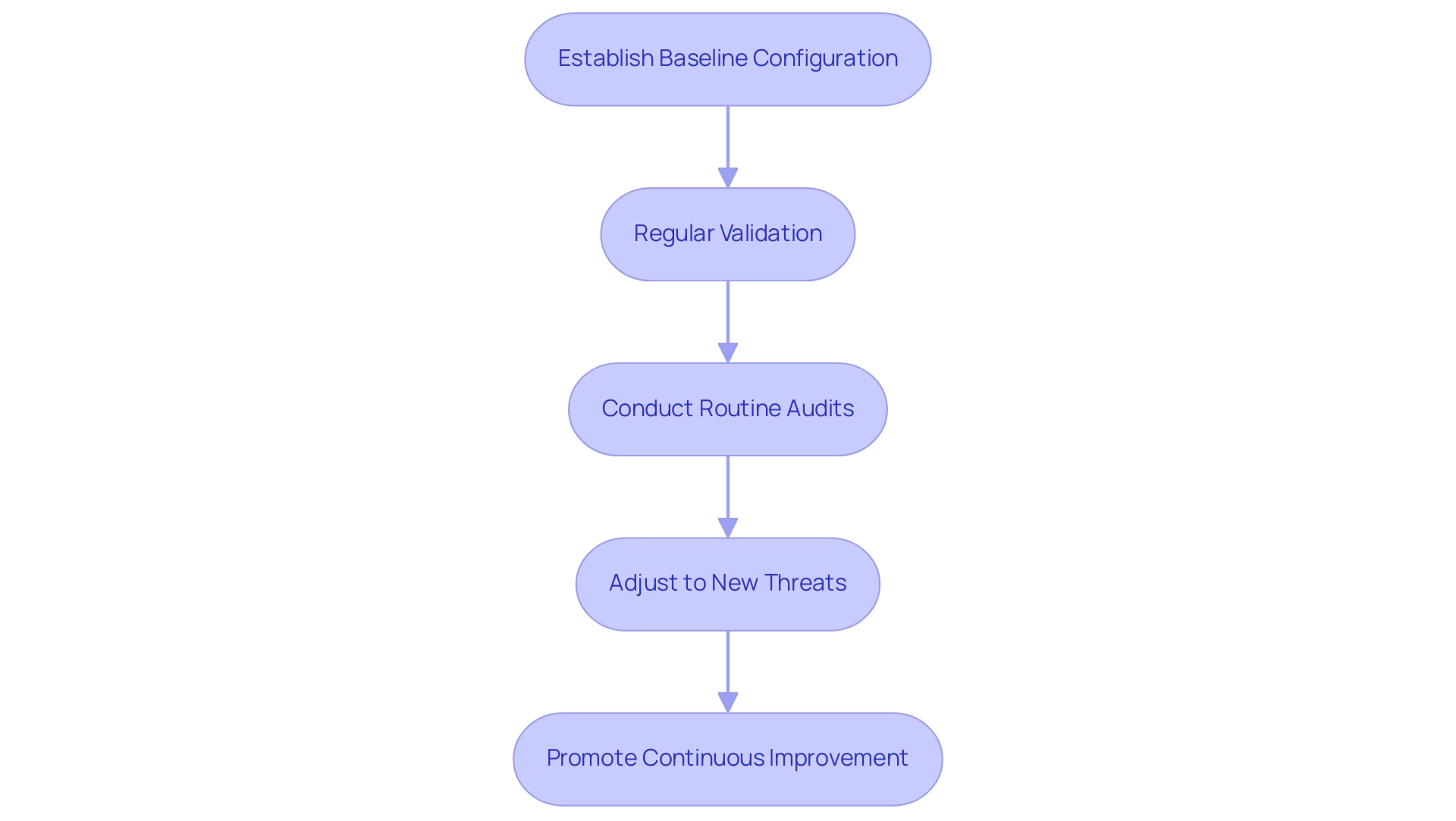
Golden configuration validation is a critical element of ensuring compliance in automated systems. This practice involves establishing a baseline configuration that meets security standards and regularly validating that automated systems tackle the automation challenge by adhering to this configuration. Manual, repetitive tasks can significantly slow down operations, leading to wasted time and resources; therefore, by implementing golden configuration validation, entities can significantly reduce the risk of security vulnerabilities that arise from misconfigured systems.
This process not only aids in adhering to regulatory requirements but also tackles the automation challenge by improving operational efficiency through Robotic Process Automation (RPA) while promoting a culture of accountability and continuous improvement within the entity. Furthermore, utilizing customized AI solutions alongside routine audits and updates to the optimal configuration is crucial for adjusting to new threats and guaranteeing that processes remain effective and secure, ultimately promoting informed decision-making and business growth.
Overcoming Resistance to Automation in Organizations
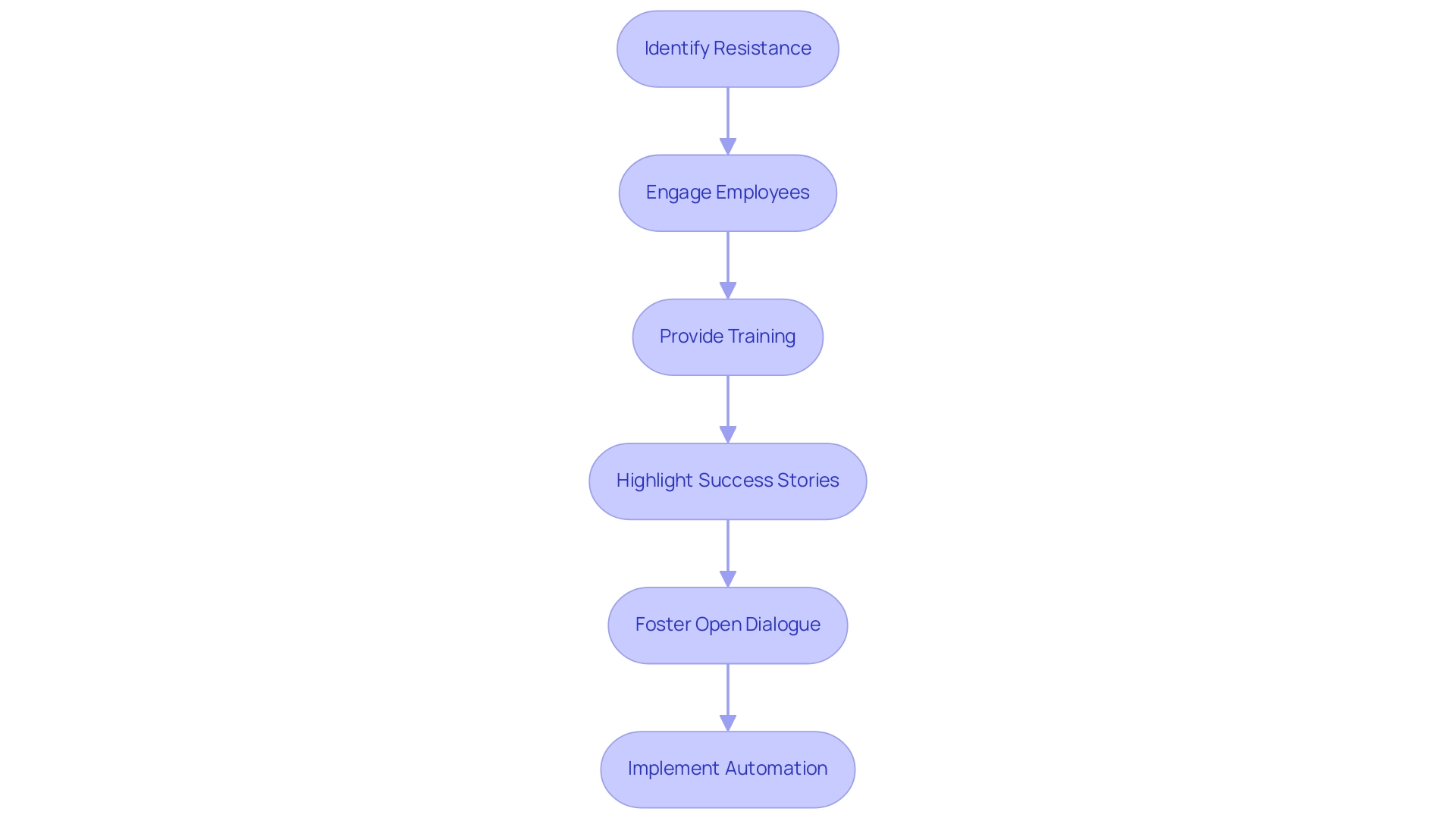
Opposition to mechanization presents an automation challenge for companies, frequently arising from fears of job loss or a lack of understanding regarding the benefits of mechanization. To overcome this resistance, it is essential to engage employees in the automation challenge from the outset. Providing training sessions that educate staff on how technologies like Robotic Process Automation (RPA) can help overcome the automation challenge by streamlining workflows, boosting efficiency, and reducing errors enhances their roles rather than replace them, fostering a more positive outlook.
Furthermore, highlighting success stories of enterprises that have effectively implemented customized AI solutions and utilized Business Intelligence to promote informed decision-making can inspire confidence. For instance, a recent case study revealed that a company reduced its processing time by 40% after integrating RPA into its operations. Fostering open dialogue and feedback during the implementation can also assist in addressing concerns related to the automation challenge and in creating a supportive atmosphere for change.
Measuring Success: Metrics for Automation Effectiveness
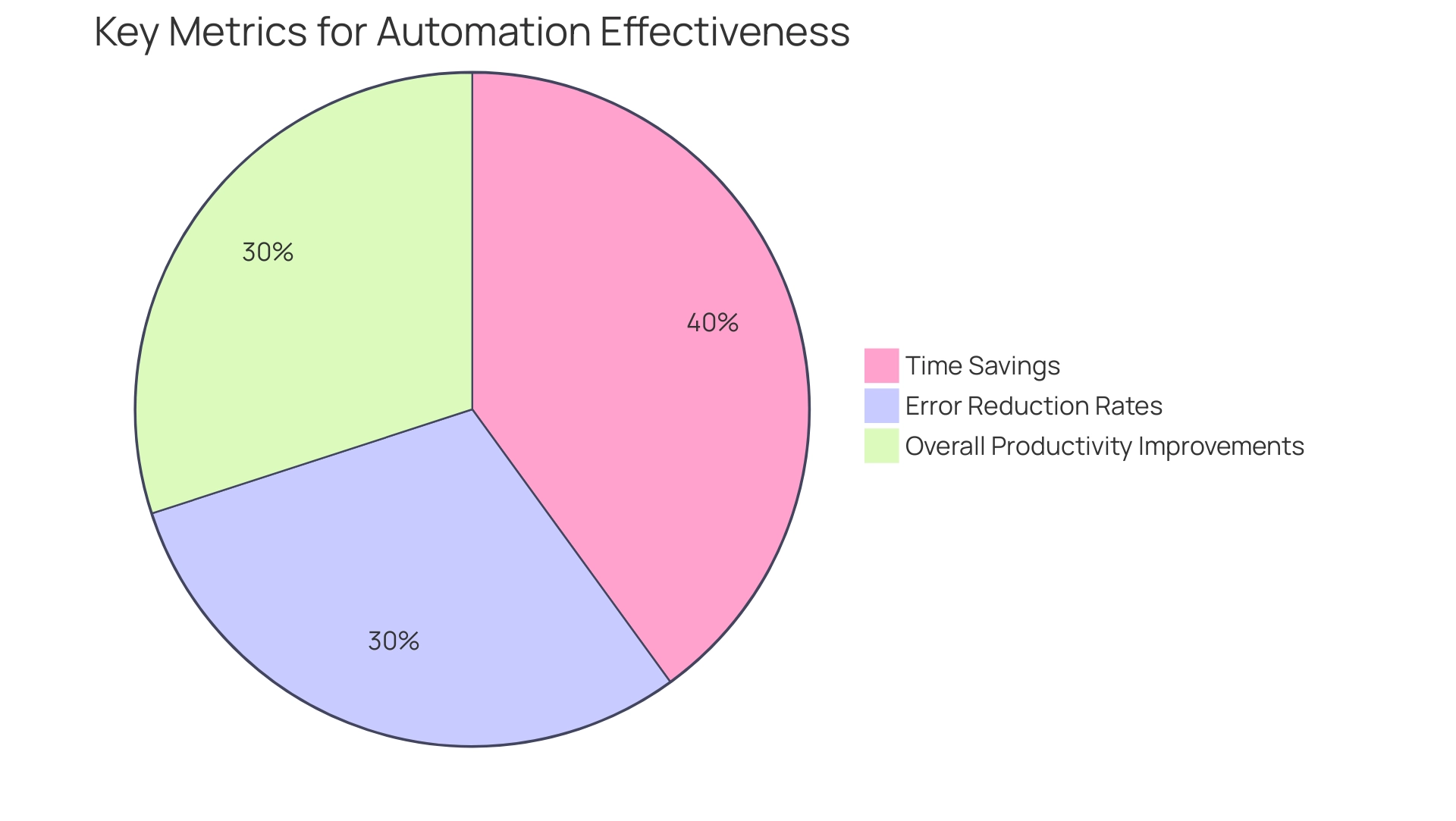
To effectively assess the success of automated initiatives, companies should define clear key performance indicators (KPIs) that address the automation challenge and align with their business goals. These metrics can encompass:
- Time savings
- Error reduction rates
- Overall productivity improvements
Particularly through the use of innovative tools like EMMA RPA, which automates repetitive tasks, and Microsoft Power Automate, which streamlines workflows. Consistently analyzing these metrics allows businesses to assess the effect of mechanization on their operational processes and make informed choices regarding future investments.
Furthermore, gathering feedback from employees utilizing the automated systems is crucial, as it provides insights into their experiences and highlights potential areas for enhancement. By continuously monitoring and refining automation strategies based on these metrics, organizations can tackle the automation challenge and optimize the benefits of their RPA efforts, ultimately enhancing overall productivity and employee morale while addressing task repetition fatigue and staffing shortages.
Conclusion
Embracing automation in security policies is a transformative journey that organizations must navigate with strategic foresight. By identifying key challenges such as integration with existing frameworks and employee resistance, businesses can proactively address potential hurdles. Engaging employees through comprehensive training and transparent communication not only alleviates fears but also highlights the significant benefits of automation, including enhanced efficiency and reduced error rates.
The importance of golden configuration validation cannot be overstated. This practice ensures compliance and operational efficiency by establishing a secure baseline configuration that automated systems must adhere to. Regular audits and updates are essential to adapting to evolving threats, fostering a culture of accountability that drives continuous improvement.
Furthermore, measuring the success of automation initiatives through clear key performance indicators is vital. By focusing on metrics such as time savings and error reduction, organizations can track the effectiveness of their automation strategies and make informed decisions for future enhancements. Continuous feedback from employees also plays a crucial role in refining these processes.
Ultimately, the integration of automation in security policies empowers organizations to modernize their operations while enabling employees to focus on more strategic tasks. By overcoming resistance, ensuring compliance, and measuring success, organizations can unlock the full potential of automation, paving the way for innovation and operational excellence. Now is the time to embrace this evolution, transforming challenges into opportunities for growth and success.