Overview:
Object Level Security (OLS) in Power BI is crucial for safeguarding sensitive data by allowing organizations to control access at the level of tables, columns, and measures. The article emphasizes that OLS not only helps in complying with privacy regulations but also enhances operational efficiency by enabling tailored access for users, thereby fostering trust and reducing the risk of unauthorized information exposure.
Introduction
In an age where data is both a valuable asset and a potential liability, Object Level Security (OLS) in Power BI emerges as a critical solution for organizations striving to protect sensitive information.
As compliance demands escalate and privacy regulations tighten, the implementation of OLS allows businesses to define precise access controls at the object level, ensuring that only authorized personnel can view sensitive data.
This strategic approach not only mitigates risks associated with unauthorized access but also fosters transparency, aligning with the growing public expectation for responsible data governance.
By integrating OLS with cutting-edge technologies like Robotic Process Automation (RPA), organizations can streamline their reporting processes while enhancing operational efficiency.
As the landscape of data security continues to evolve, understanding and applying OLS will empower organizations to navigate compliance challenges and bolster their data protection strategies effectively.
Understanding Object Level Security in Power BI
Object level security in Power BI is essential for protecting sensitive information as it allows entities to implement access controls at the object level, which includes tables, columns, and measures. This functionality is not just a technical enhancement; it is essential for ensuring compliance with increasingly stringent privacy regulations. In today’s information-rich environment, organizations must also be aware of privacy concerns associated with uploading images containing embedded location details (EXIF GPS), as this information can be extracted by visitors.
With 72% of businesses currently employing compliance solutions to navigate privacy law requirements, the implementation of object level security in Power BI becomes a strategic necessity. For example, a financial services company might limit access to customer financial information using object level security in Power BI, ensuring that only authorized personnel can view this sensitive content, while others can access only non-sensitive details. This practice not only reduces the risk of unauthorized information exposure but also aligns with the desires of 76% of the US population for greater transparency in information usage, highlighting the critical need for entities to communicate clearly about access.
As Osman Husain, a content lead at Enzuzo, aptly notes, ‘This indicates a failing on behalf of the industry as informed consent is a cornerstone of effective compliance.’ Furthermore, with 43% of websites employing tactics to nudge users towards accepting all cookies, entities must prioritize transparency to foster trust. Along with OLS, entities encounter difficulties in deriving insights from Power BI dashboards, including lengthy report generation and inconsistencies in information.
By integrating Business Intelligence and RPA solutions, companies can streamline their reporting processes and enhance operational efficiency. By adopting object level security in Power BI alongside robust Business Intelligence strategies, entities not only enhance their information protection measures but also build trust with stakeholders, reinforcing their commitment to responsible information governance and operational efficiency.
Practical Applications and Use Cases of Object Level Security
The practical applications of object level security in Power BI are extensive and impactful. In healthcare, for example, OLS can be employed to ensure that patient records are accessible only to authorized personnel, maintaining compliance with HIPAA regulations. This not only safeguards sensitive patient information but also reduces the risk of expensive breaches, which average nearly $11 million in the healthcare sector.
A recent case study titled ‘How to Prepare Your Entity to Avoid Vulnerabilities in 2024’ emphasizes that remediating cybersecurity vulnerabilities is an urgent priority for entities. In the retail sector, OLS can strategically restrict access to sales information by geographic area, allowing regional managers to view only the details relevant to their operations while protecting sensitive details from competitors. Additionally, in financial reporting, various stakeholders frequently need different levels of detail; OLS supports the development of tailored reports that satisfy these unique requirements.
By utilizing OLS alongside Robotic Process Automation (RPA), entities can improve safety and usability, cultivating an atmosphere where enhanced decision-making and operational efficiency flourish. RPA not only streamlines repetitive tasks, reducing errors, but also frees up team resources for more strategic initiatives, allowing them to focus on high-value work. OLS ensures that sensitive information is protected while enabling this efficiency.
The capability to implement detailed access controls through OLS is not merely a protective measure; it’s a strategic asset entities must utilize to remain competitive in an ever more interconnected and susceptible environment. However, organizations often face challenges when leveraging insights from Power BI dashboards, such as time-consuming report creation and data inconsistencies. Addressing these challenges is crucial for maximizing the value of BI solutions.
With the growing number of known spear-phishing groups and the alarming statistics around supply chain attacks, the urgency to prioritize protective measures like object level security in Power BI becomes even more evident. Moreover, as emphasized in a study of 24 incidents, over 50% of supply chain attacks were linked to prominent cyber crime groups, highlighting the necessity for strong protective measures, including object level security in Power BI. It is also crucial to note that penetration testing is essential for understanding vulnerabilities in interconnected computer systems, further reinforcing the importance of object level security in Power BI as an integral part of a broader protection strategy.
Implementing Object Level Security in Power BI
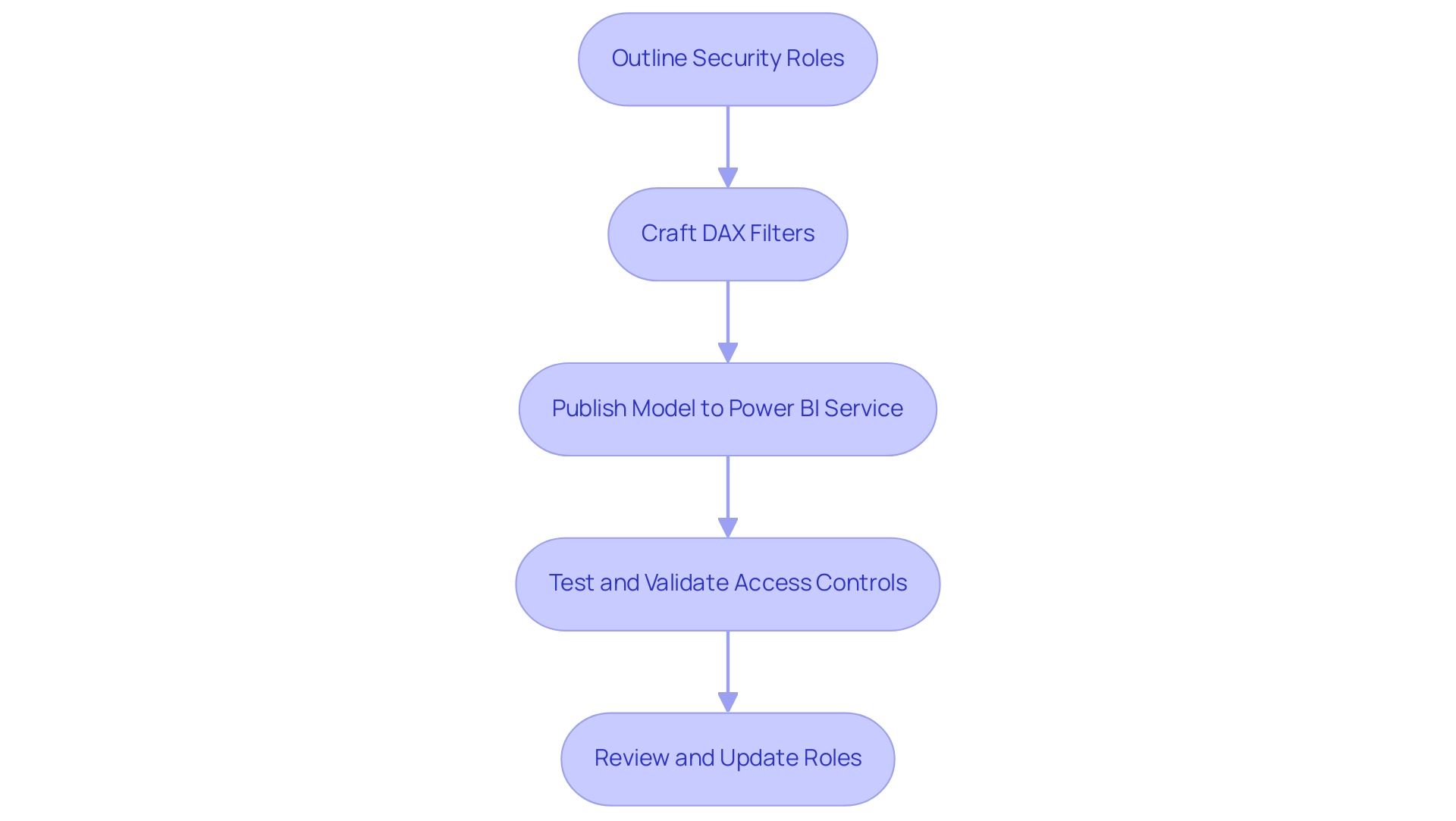
Implementing object level security in Power BI entails several crucial steps that empower organizations to manage access effectively while addressing common challenges such as time-consuming report creation, inconsistencies, and the lack of actionable guidance in reports. The process starts with outlining the specific security roles that will determine access to designated objects within the model. This can be accomplished in Power BI Desktop by selecting the ‘Modeling’ tab and clicking on ‘Manage Roles.’
Once roles are established, the next step involves crafting DAX (Data Analysis Expressions) filters to delineate the information each role can access. For instance, a DAX filter might be employed to restrict a sales manager’s visibility to sales information pertinent solely to their designated region. After establishing roles and filters, it is crucial to publish the model to the Power BI service, where the applied access controls can be thoroughly tested and validated.
Consistently reviewing and updating these roles is essential to adjust to changes within the organizational structure or shifts in information sensitivity. By following these guidelines, organizations can effectively leverage object level security in Power BI, thereby enhancing their security posture and ensuring compliance with privacy standards. Furthermore, OLS not only assists in concealing sensitive information but also enables the creation of actionable insights by ensuring that users have access to the most pertinent details for their roles.
As mentioned in recent discussions, the introduction of object level security in Power BI has been a game-changer since its release in February 2021, allowing users to hide not only columns and tables but also derived calculations like measures and calculated columns, thus providing an additional layer of protection. This capability is essential for driving data-driven insights that lead to informed decision-making, ultimately driving growth and operational efficiency. As Sapana Taneja remarked, ‘I hope you found this article helpful!’
This sentiment reflects the importance of sharing knowledge on such pivotal topics. Furthermore, during an Unplugged session lasting 45:22, experts discussed the practical implications of object level security in Power BI, emphasizing its role in improving data protection and addressing the challenges associated with data governance. A case study on object level security in Power BI highlights how users can set security roles within Power BI Desktop and test the user experience, showcasing the effectiveness of object level security in Power BI in real-world scenarios.
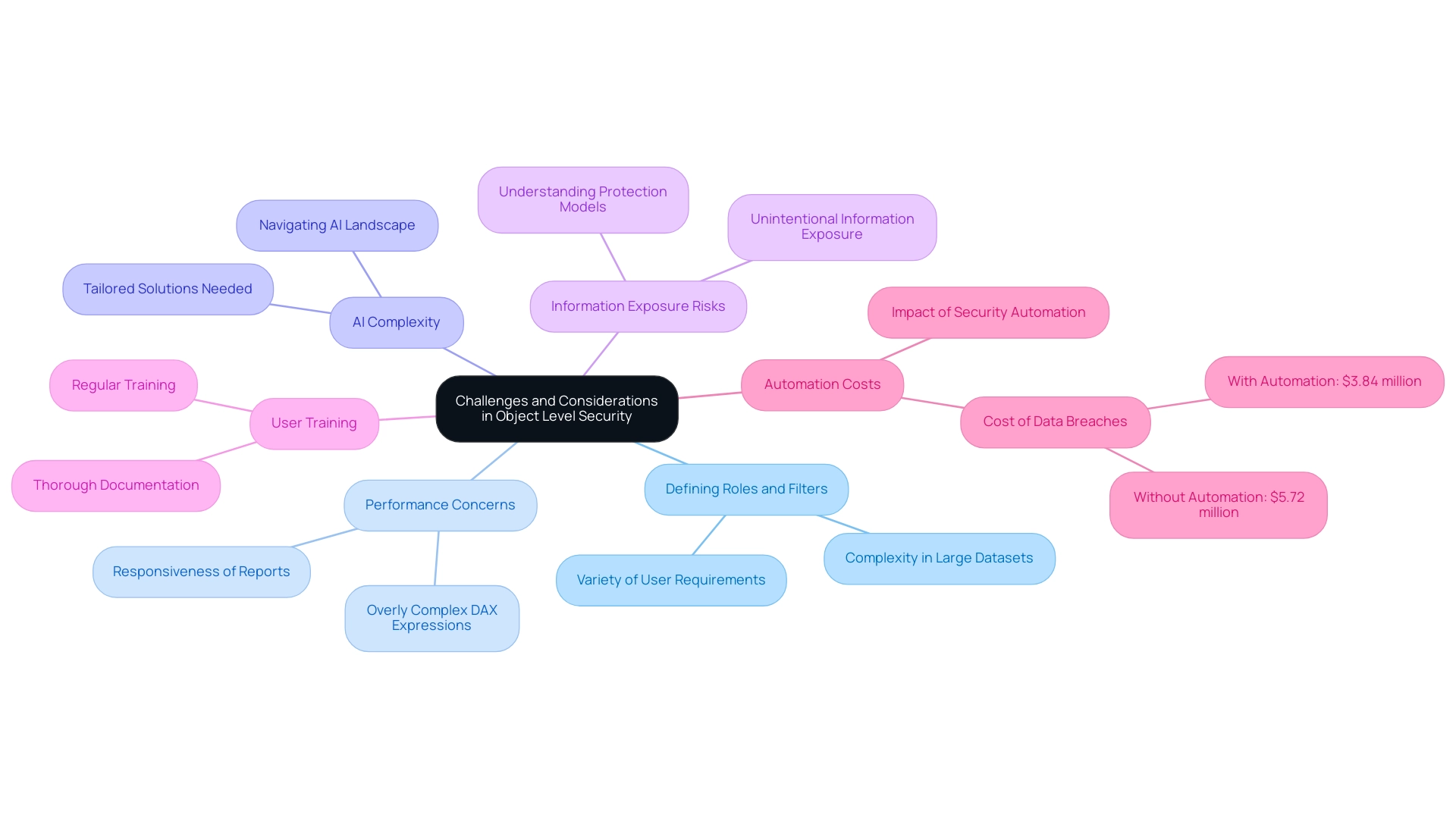
Challenges and Considerations in Object Level Security
Implementing object level security in Power BI within enterprises can yield significant advantages, yet several challenges often arise during its deployment. One prevalent issue is the intricacy involved in defining roles and filters, particularly in expansive datasets that cater to a variety of user requirements. Performance concerns may also emerge, especially if organizations rely on overly complex DAX expressions, which can hinder the responsiveness of Power BI reports.
Furthermore, navigating the overwhelming AI landscape necessitates tailored solutions that simplify these complexities, enhancing efficiency through tools like Robotic Process Automation (RPA). The risk of unintentional information exposure emphasizes the necessity of ensuring that all users understand the protection model effectively. With the average company sharing confidential information with 583 third-party vendors, the urgency of implementing robust protective measures cannot be overstated.
Regular training and thorough documentation play a crucial role in alleviating these obstacles; studies indicate that effective user training significantly enhances security awareness. Organizations should also prioritize the periodic review of their object level security in Power BI configurations to maintain their relevance and efficiency as business needs evolve. The challenges in leveraging insights from Power BI dashboards, such as time-consuming report creation and inconsistencies, can be effectively addressed through our 3-Day Power BI Sprint.
This service is designed to create professional reports quickly, focusing on actionable outcomes and ensuring that teams can leverage insights without the burden of extensive report-building processes. By providing a structured method for report creation, the 3-Day Power BI Sprint enables companies to streamline their reporting efforts, ultimately enhancing decision-making capabilities. Based on a case study examining the average expense of breaches related to automation levels, entities with significant use of automation encountered an average cost of $3.84 million in 2024, in contrast to $5.72 million for those without automation.
As Nick Rago, Field CTO at Salt Security, notes, ‘In many instances, the barrier to breach was pretty low, and the attacker did not need any herculean effort to take advantage of a misconfigured API.’ By proactively tackling these challenges and leveraging tailored AI solutions, organizations can fully utilize the benefits of object level security in Power BI while effectively minimizing associated risks.
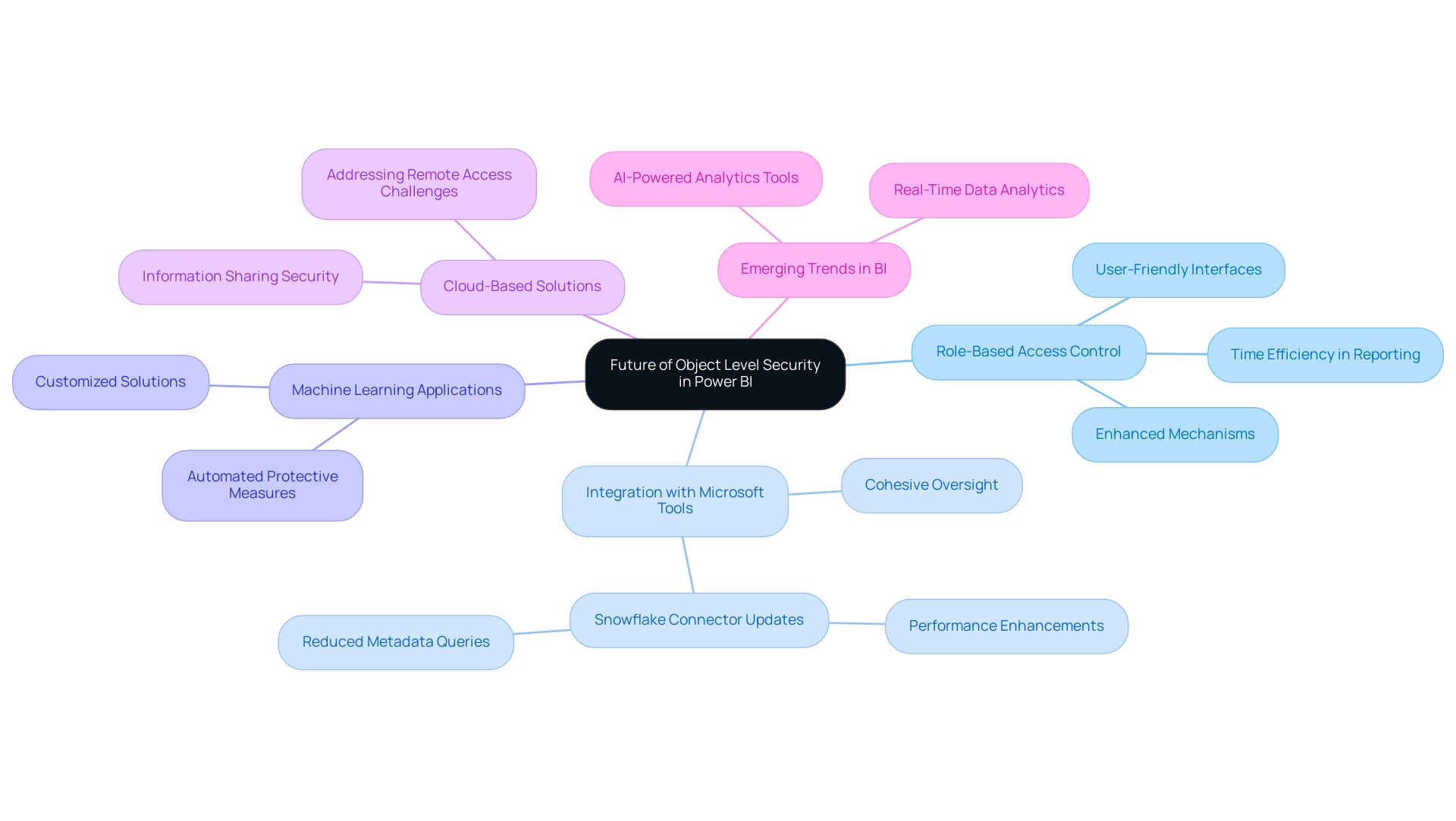
The Future of Object Level Security in Power BI
As the environment of information protection changes, notable progress is expected in object level security in Power BI, which will directly address typical challenges faced by Directors of Operations Efficiency. The enhanced role-based access control (RBAC) mechanisms guarantee that sensitive information is available solely to permitted individuals, highlighting the significance of protection in information access while decreasing the time invested in creating reports. Future advancements are anticipated to showcase more user-friendly interfaces for defining roles and filters, optimizing the management process and assisting in reducing inconsistencies.
Improved integration with other Microsoft protection tools is also on the horizon, offering a cohesive approach to oversight across platforms. Significantly, the incorporation of machine learning algorithms could transform how sensitive information is recognized, automating the suggestion of suitable protective measures customized to particular organizational requirements. With the growing adoption of cloud-based solutions, OLS will likely adjust to address new security challenges arising from remote access and information sharing, particularly through the use of object level security in Power BI.
For instance, recent updates to the Snowflake connector have enhanced efficiency in information handling and connectivity, showcasing practical advancements relevant to object level security in Power BI. Furthermore, as entities navigate the overwhelming options in the AI landscape, tailored AI solutions can help cut through the noise, aligning technologies with specific business goals and challenges. Insights from the community highlight emerging trends in Business Intelligence (BI), including the future of real-time information analytics and the necessity of AI-powered analytics tools.
By actively remaining aware of these trends, companies can enhance their information protection approaches, guaranteeing adherence and strong defense in a constantly changing digital environment. Jason Himmelstein stresses the urgency of these advancements, stating, ‘Users can now update their visuals in real time, interact with their information through Power BI’s standard features such as filtering, cross-highlighting, and tooltips.’ This adaptability is crucial as organizations prepare for the future of data security in 2024 and beyond.
Conclusion
Implementing Object Level Security (OLS) in Power BI is not just a technical necessity; it’s a strategic imperative for organizations aiming to safeguard sensitive data while fostering a culture of transparency and trust. By defining precise access controls at the object level, businesses can ensure that only authorized personnel have access to critical information. This capability is particularly vital in today’s regulatory environment, where compliance with data privacy laws is paramount.
The practical applications of OLS across various industries, from healthcare to finance, illustrate its versatility in enhancing data protection. By tailoring access to sensitive information, organizations can mitigate risks associated with unauthorized data exposure, ultimately protecting their assets and reputation. Moreover, integrating OLS with Robotic Process Automation (RPA) streamlines reporting processes, allowing teams to focus on high-value tasks and improving operational efficiency.
While challenges such as defining roles and managing complex datasets exist, organizations can overcome these hurdles with regular training, comprehensive documentation, and periodic reviews of their security configurations. By adopting a proactive approach to OLS implementation, organizations can not only enhance their security posture but also drive informed decision-making through actionable insights.
As the landscape of data security continues to evolve, the future of OLS in Power BI looks promising. Anticipated advancements in role-based access control, user interface improvements, and enhanced integrations with security tools will further empower organizations to navigate the complexities of data governance. Staying ahead of these trends will be crucial for organizations committed to robust data security and compliance in an increasingly interconnected world.