Introduction
In an age where data breaches dominate headlines and privacy concerns escalate, organizations are compelled to adopt stringent measures to protect sensitive information. Row-Level Security (RLS) emerges as a crucial solution, enabling businesses to control data access at an unprecedented level of granularity. By ensuring that users only access data pertinent to their roles, RLS not only fortifies compliance with evolving regulations but also enhances overall data governance.
As industries grapple with the complexities of cybersecurity, understanding and implementing RLS can transform how organizations safeguard their most valuable assets. This article delves into the fundamentals of RLS, its myriad benefits, technical insights, practical applications, and the challenges organizations face in its implementation, providing a comprehensive guide for those looking to bolster their data security frameworks.
Defining Row-Level Security: An Overview
Row-level security (RLS) is a vital database protection feature that ensures users can only access information they are specifically authorized to view, thereby effectively restricting information retrieval at the row level. This capability is essential in settings managing sensitive information, as it reduces the risks presented by unauthorized entry. For example, as highlighted by American politician Marco Rubio, former employees holding onto sensitive company information can create significant vulnerabilities, emphasizing the urgent need for strong information management.
In today’s digital environment, where customer discontent can spread across social networks—potentially reaching 6,000 acquaintances per dissatisfied client—organizations must prioritize information protection to uphold their reputation and trust. Row-level security (RLS) operates by implementing policies that filter information based on user roles or characteristics, resulting in customized views that align with individual privileges. This level of granularity not only fortifies compliance with protection regulations but also enhances overall governance.
The case study titled ‘Data Access Risks’ illustrates how organizations have faced security vulnerabilities due to inadequate access controls, emphasizing the need for strict measures. By implementing row-level security, organizations can maintain the integrity and confidentiality of their sensitive information, thereby protecting against potential breaches and ensuring a secure operational environment.
The Benefits of Implementing Row-Level Security in Databases
Implementing row-level security in databases offers significant benefits that extend beyond fundamental protection. It not only strengthens information security by implementing row-level security to ensure that users retrieve only the details pertinent to their roles, but it also plays a crucial part in enhancing adherence to regulations such as GDPR and HIPAA. In 2023, the education sector encountered over 700,000 cybersecurity threats, with ransomware attacks more than doubling since 2021, resulting in an average breach cost of $3.7 million.
These concerning statistics emphasize the immediate necessity for efficient information control mechanisms. Organizations that implement row-level security (RLS), alongside Robotic Process Automation (RPA) and Business Intelligence (BI), can reduce the risk of information breaches and unauthorized entry while enhancing operational efficiency. RPA can automate repetitive information management tasks, such as handling user permissions and monitoring access logs, allowing teams to concentrate on strategic initiatives that foster growth.
Furthermore, integrating BI tools transforms raw information into actionable insights, utilizing row-level security to empower informed decision-making. In addition to RLS, strengthening cybersecurity through regular audits, establishing backup systems, and utilizing endpoint protection is essential for comprehensive security. This not only promotes greater accountability and transparency within teams but also aligns with regulatory compliance requirements, simplifying adherence to stringent protection laws.
As noted by industry experts, adopting row-level security significantly enhances operational efficiency. A culture of responsible data management emerges when access is strictly monitored, leading to improved decision-making capabilities and operational agility. In a landscape where organizations with managed service providers experienced a 21% shorter breach lifecycle, the implementation of row-level security (RLS) is a proactive measure to protect sensitive information and strengthen overall organizational resilience.
The education sector’s limited cybersecurity resources make it an appealing target for cybercriminals, and many attacks are preventable through basic protective measures, which highlights the critical role of row-level security in a broader defense strategy.
How Row-Level Security Works: Technical Insights
Row-level security (RLS) serves as a crucial approach for managing access to information at a granular level. It is executed through guidelines that specify which rows a user can view, depending on their role or particular attributes, thereby ensuring row-level security. In SQL databases, row-level security (RLS) is typically established using functions designed to return a boolean value, which determines whether a user is permitted to view a particular row.
This is achieved by generating protection criteria that sift information based on user traits. Furthermore, integrating row-level security (RLS) with established database protection measures, such as role-based access control (RBAC), enables organizations to adopt a comprehensive, multi-layered approach to safeguarding. This integration not only enhances data protection but also addresses technical challenges that may arise during the implementation of row-level security.
With over 4 million satisfied learners, DigitalDefynd demonstrates the growing importance of understanding row-level security in today’s data-driven environment. As Eric Raymond aptly stated, ‘Being able to break into systems doesn’t make you a hacker any more than being able to hotwire cars makes you an automotive engineer.’ This emphasizes the necessity for strong protection measures such as row-level security.
Moreover, as the future of cybersecurity will involve regular exercises and assessments mandated by regulators, understanding these technical elements becomes crucial for organizations to effectively leverage row-level security to strengthen their cybersecurity frameworks and meet the evolving demands of privacy and security.
Common Use Cases for Row-Level Security
Row-level security (RLS) is essential for safeguarding sensitive data across various industries, such as healthcare, finance, and education, where confidentiality is of utmost importance. In the healthcare sector, for example, the implementation of row-level security ensures that patient records are accessible solely to authorized medical personnel, thereby upholding patient privacy and adhering to regulatory standards. Real-world applications of RLS in healthcare demonstrate its critical function in protecting patient privacy.
Likewise, in the financial sector, banks and financial institutions utilize row-level security (RLS) to restrict entry to sensitive financial information based on user roles, significantly diminishing the risk of fraud and enhancing compliance with stringent regulations. This flexible approach is highlighted by the fact that RLS policies can be attached to multiple tables, allowing for a scalable implementation tailored to specific needs. Educational institutions can also benefit from row-level security by managing entry to student records, ensuring that only authorized staff members can view sensitive information.
As Ganesh Kirti, founder and CEO of TrustLogix, observes,
The new row-level protection features will enable our clients to accurately specify information control measures based on their business entitlements while abstracting them from the technical complexities.
A practical example of row-level security (RLS) in action is presented in the case study titled ‘Enabling and Disabling Row-Level Security,’ which demonstrates how administrators can dynamically manage information retrieval on specific tables, ensuring adherence to policies. These diverse use cases illustrate the significant impact of row-level security (RLS) in enhancing information security and compliance across various sectors, underscoring its necessity in today’s information-driven landscape.
Challenges and Considerations in Implementing Row-Level Security
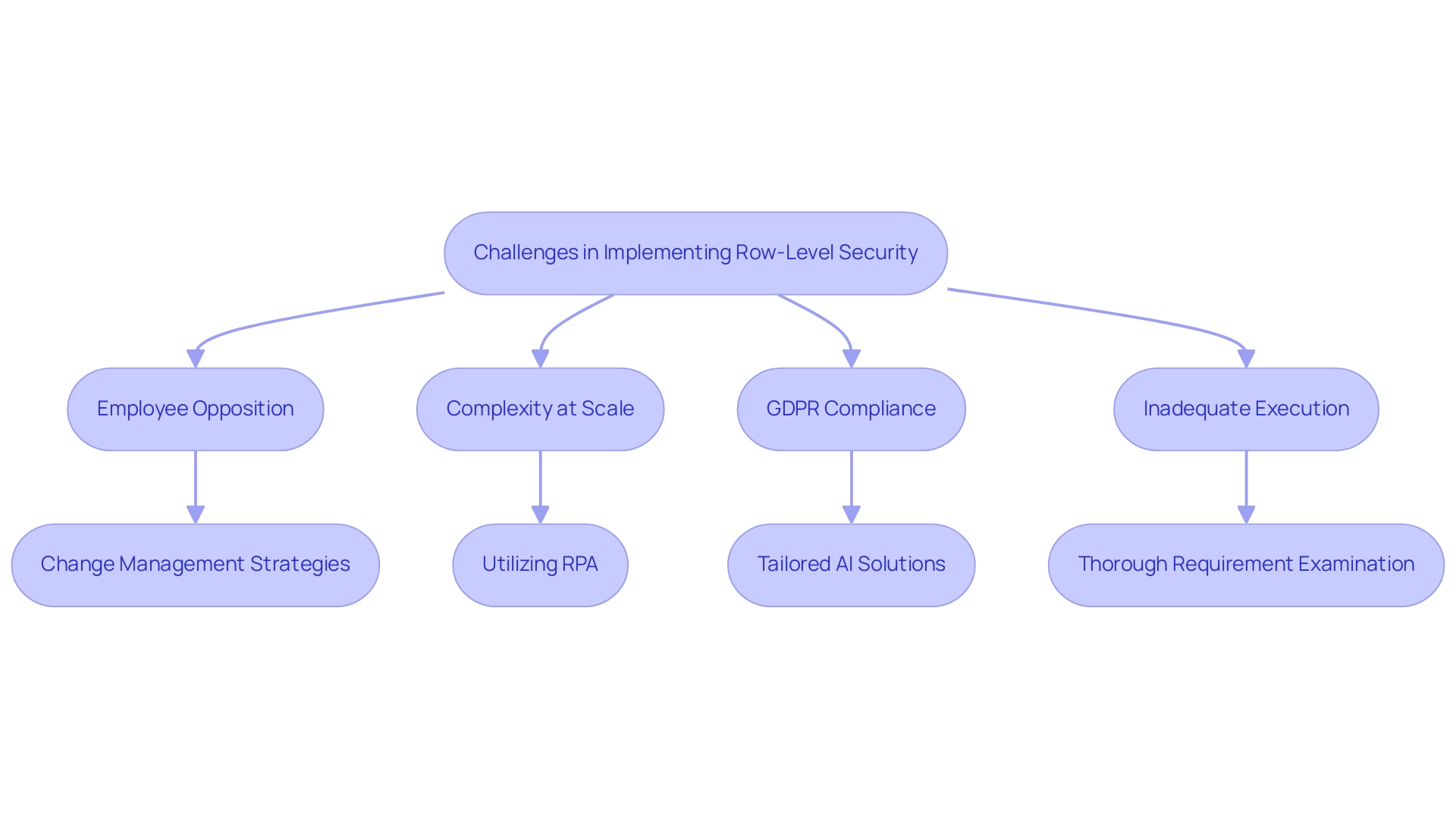
Implementing row-level security (RLS) provides organizations with numerous advantages, but it also introduces significant challenges that require careful navigation. One significant obstacle is employee opposition, especially from those who are used to unrestricted information availability. Statistics indicate that a significant portion of employees may resist alterations to information retrieval controls, fearing that it could hinder their productivity.
Therefore, robust change management strategies are essential to facilitate a smooth transition to more restricted entry protocols. As highlighted by Lisa Levy, a Content Specialist, ‘While there are many benefits associated with Postgres RLS, in some cases it is difficult to maintain, especially at scale.’ This complexity is heightened in organizations with large and varied datasets, making the implementation of row-level security a challenging endeavor.
Moreover, organizations must ensure GDPR compliance, as RLS alone may not offer sufficient protections like pseudonymization or encryption, raising concerns about information safety. To effectively navigate these challenges, it is crucial for organizations to conduct a thorough examination of their information retrieval requirements prior to implementing row-level security. This ensures that security policies are robust and aligned with the organization’s broader goals.
Moreover, utilizing Robotic Process Automation (RPA) can enhance the management of information retrieval, automating repetitive tasks related to compliance and control, which can ease some of the burdens associated with RLS implementation. Tailored AI solutions can also assist organizations in identifying and addressing specific challenges, ensuring that data protection regulations like GDPR are met. By referencing real-world case studies, organizations can better understand challenges such as coding bottlenecks, conflicts with existing access control measures, and potential performance issues.
Inadequate execution can result in vulnerabilities and decreased database performance. By proactively addressing these challenges with RPA and AI, organizations can leverage row-level security to significantly enhance their data security posture while minimizing disruptions, ultimately fostering a culture of informed decision-making driven by Business Intelligence and operational efficiency enabled by RPA.
Conclusion
Implementing Row-Level Security (RLS) offers organizations a robust framework for safeguarding sensitive data, ensuring that only authorized users can access information relevant to their roles. This granular level of control not only fortifies compliance with critical regulations like GDPR and HIPAA but also enhances overall data governance. The urgency for such measures is underscored by alarming statistics regarding cybersecurity threats, particularly in sectors such as education, healthcare, and finance, where the stakes are exceptionally high.
However, while the benefits of RLS are clear, organizations must navigate several challenges during implementation. Employee resistance to change, the complexity of managing extensive datasets, and ensuring compliance with data protection laws are significant hurdles that require strategic planning and effective change management. Leveraging automation tools like Robotic Process Automation (RPA) can streamline the transition, allowing organizations to focus on their core objectives while maintaining robust security protocols.
Ultimately, the integration of RLS into data security frameworks is not just a technical upgrade; it represents a cultural shift towards responsible data management. By prioritizing RLS, organizations can not only protect their most valuable assets but also foster a culture of accountability and informed decision-making. In a landscape where data breaches can have devastating consequences, the proactive adoption of RLS is essential for building resilience and trust in today’s data-driven world.

