Overview
The article provides a comprehensive guide on how to implement Object Level Security (OLS) effectively, emphasizing the importance of granular access control, role-based access control, and audit trails in protecting sensitive information. It outlines a step-by-step process for implementation, including assessing current security measures, defining user roles, selecting appropriate tools, and conducting ongoing training and audits, thereby highlighting that a structured approach is crucial for enhancing data protection and operational efficiency in organizations.
Introduction
In an age where data breaches and cyber threats loom large, organizations are increasingly turning to Object Level Security (OLS) as a crucial defense mechanism. OLS not only regulates access to sensitive information but also enhances operational efficiency by ensuring that employees have the necessary permissions to perform their roles effectively.
With the rise of stringent data protection regulations and the alarming statistics surrounding internal vulnerabilities, understanding the core concepts of OLS—such as:
- Granular access control
- Role-based access control
- The importance of audit trails
has never been more essential. As organizations seek to bolster their security protocols, the implementation of OLS emerges as a vital strategy for safeguarding data integrity and fostering a culture of compliance in an ever-evolving digital landscape.
Understanding Object Level Security: Key Concepts and Definitions
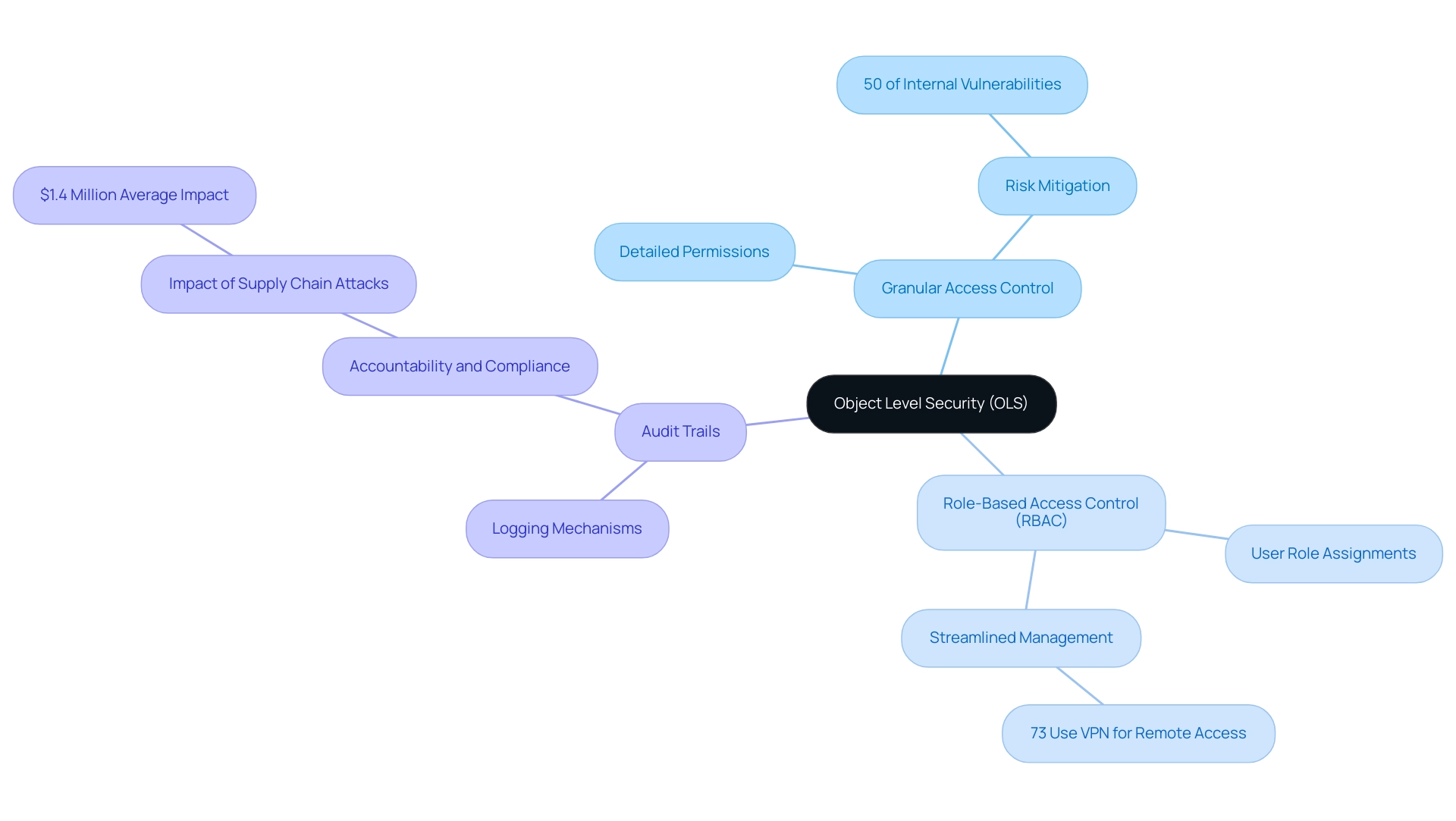
Object level security (OLS) encompasses the strategies and mechanisms that manage access to individual objects within a database or application, including files, records, and various information entities. By implementing object level security, organizations can ensure that only authorized users can utilize or manipulate specific objects in accordance with their designated roles and permissions. The key concepts of OLS include:
- Granular Access Control: This feature allows organizations to establish highly detailed access permissions, ensuring users can only access data that is essential for their roles. This is becoming increasingly essential as 50% of internal application vulnerabilities are categorized as high or critical risks, highlighting the need for targeted protective measures.
- Role-Based Access Control (RBAC): A prevalent approach within object level security, RBAC assigns permissions based on user roles rather than individual identities, thereby streamlining management processes. Considering that 73% of organizations depend on VPN connections for remote connectivity, RBAC can greatly improve security by limiting information retrieval to authorized individuals only, particularly in settings where remote connectivity is prevalent and presents additional risks.
- Audit Trails: Object level security typically includes logging mechanisms that meticulously track access and modifications made to objects, thereby fostering accountability and supporting compliance efforts. In an environment where the average financial impact of a supply chain attack reached $1.4 million in 2021, maintaining comprehensive audit trails is essential for organizations aiming to protect their integrity.
Grasping these concepts is crucial for effectively implementing object level security and enhancing data protection protocols within any organization. The origins of cyber attacks, particularly from countries like China and Russia, highlight the critical nature of OLS; social engineering tactics, especially phishing, are implicated in 90% of breaches. As highlighted by expert Aneesh Bhargav, continual learning is essential in today’s digital landscape: ‘Never stop learning with AppSecEngineer!’
This serves as a reminder that organizations must prioritize the integration of robust object level security practices and ongoing education on security measures.
The Importance of Object Level Security in Data Protection
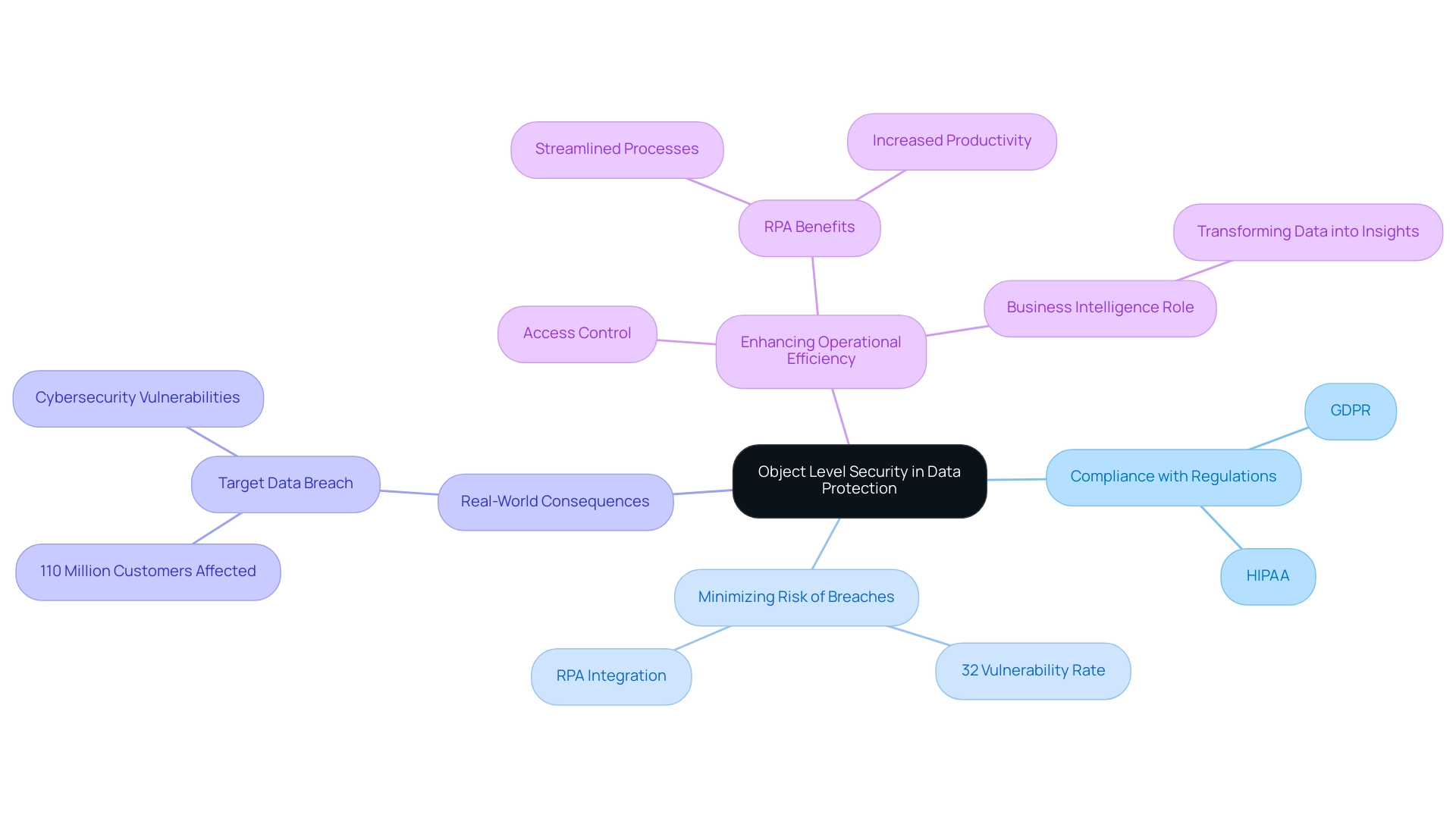
Object level security is crucial in protecting sensitive information from unauthorized entry and potential breaches, especially in a landscape where Robotic Process Automation (RPA) and Business Intelligence are increasingly vital for operational efficiency. Its importance is highlighted by several key factors:
- Compliance with Regulations: With industries facing stringent information protection regulations such as GDPR and HIPAA, OLS helps organizations adhere to these standards by ensuring that only authorized personnel can retrieve sensitive information, thus mitigating compliance risks.
- Minimizing Risk of Breaches: Implementing object level security can dramatically lower the likelihood of information breaches. Combined with RPA, which automates manual workflows and decreases human errors, organizations can improve their protective measures while streamlining processes. Object level security (OLS) ensures tight control and monitoring of privileges, thereby protecting against the alarming statistic that 32% of vulnerabilities in internet-facing applications are rated as high or critical.
- Real-World Consequences: A case study that illustrates the importance of OLS is the Target Data Breach, where cyber attackers used malware to steal information from Target’s point of sale systems, compromising details for approximately 110 million customers. This incident emphasizes weaknesses in retail cybersecurity and the crucial necessity for thorough protective measures.
- Enhancing Operational Efficiency: Apart from safeguarding information, implementing object level security aids in operational efficiency by granting employees the access they need to execute their tasks effectively, without unnecessary obstacles. Utilizing RPA in conjunction with OLS can further boost productivity, facilitating a balanced approach between protection and accessibility. RPA not only streamlines processes but also frees up team members for more strategic, value-adding work. Furthermore, Business Intelligence plays a crucial role in transforming raw data into actionable insights that inform decision-making, ensuring that object level security is not just a compliance tool, but also a facilitator of informed strategic choices. In essence, object level security is an indispensable element of a comprehensive data protection strategy, especially in a rapidly evolving AI landscape. Organizations aiming to strengthen their protective stance should view object level security not just as a compliance tool but as a fundamental aspect of their operational framework, enhanced by tailored AI solutions and RPA for informed decision-making. As Gartner notes, cloud protection statistics reveal that 25% of the world’s total cyber attacks are cloud-related incidents, further emphasizing the need for robust practices like OLS in cloud environments.
Preparing for Implementation: Tools and Requirements for OLS
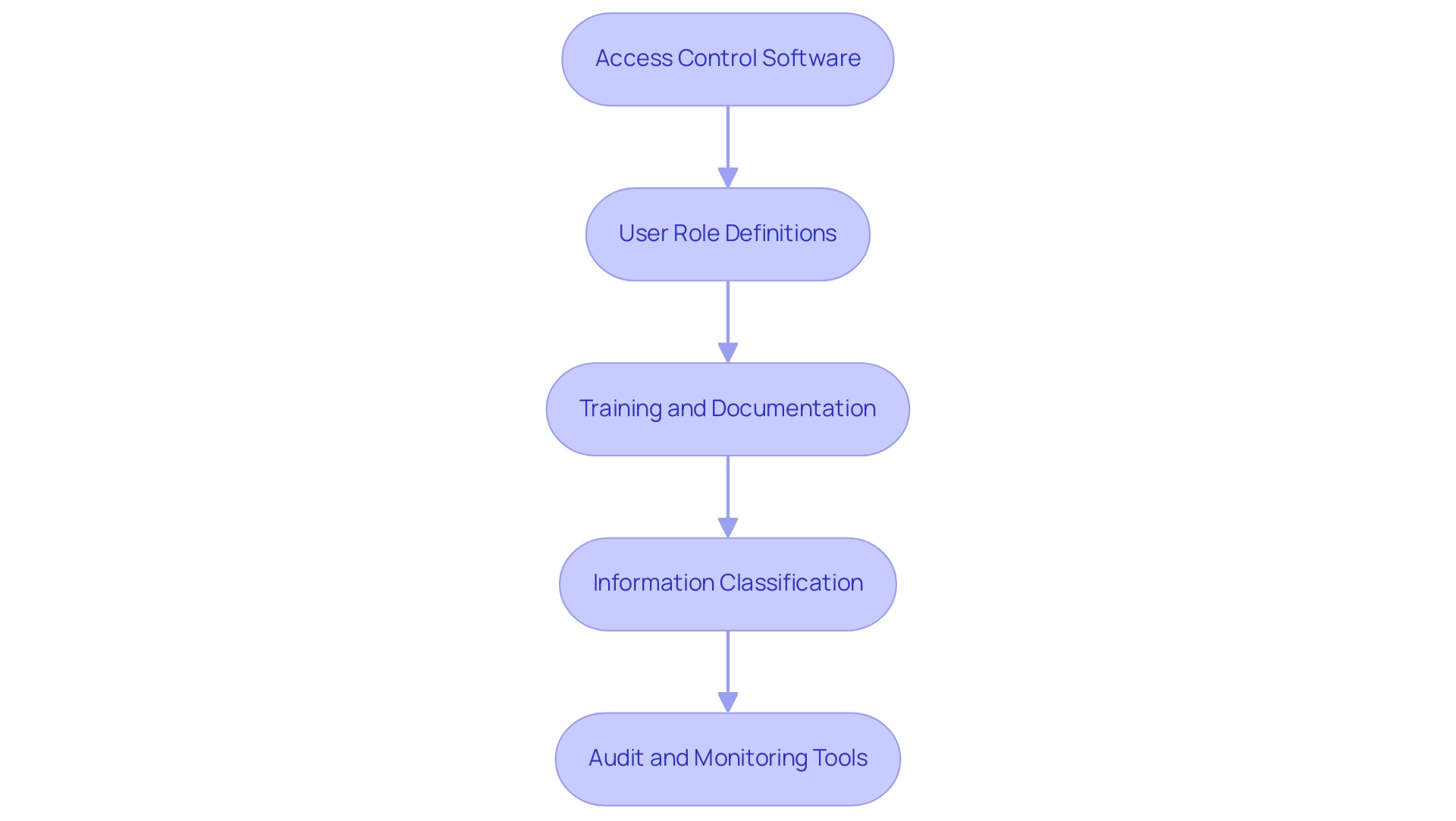
Before embarking on the implementation of Object Level Security (OLS), organizations should take several essential steps to ensure a smooth and effective process:
-
Access Control Software: Invest in robust access control software that enables granular access management. This software should be compatible with existing systems to streamline integration and enhance security frameworks. For example, the free version of Tabular Editor (Tabular Editor 2) offers essential features for managing Power BI models, making it a valuable tool in this context. Implementing such technologies can enhance operational efficiency, reducing time spent on manual tasks.
-
User Role Definitions: Clearly delineate user roles within the organization. This clarity is essential as it dictates the permission levels for various data objects, ensuring that users only engage with information relevant to their functions. As emphasized in discussions regarding object level security, defining user roles is crucial for establishing effective control over entry. As one expert aptly stated, “Here comes the Object-level security feature to the rescue!” By customizing control according to specific roles and ensuring object level security, organizations can reduce confusion and improve compliance.
-
Training and Documentation: Provide comprehensive training for staff on object level security principles and protocols. Coupled with detailed documentation, this training will serve as a valuable resource, helping users navigate the complexities of OLS effectively. This step is crucial in overcoming technology implementation challenges, ensuring that employees are well-equipped to utilize these systems with object level security effectively.
-
Information Classification: Conduct a thorough information classification exercise to identify sensitive objects within the information model. This step is vital for establishing which elements require object level security, thereby minimizing the risk of unauthorized access. Utilizing Business Intelligence tools can assist in converting raw information into actionable insights, facilitating this classification process. This process also addresses the challenges of extracting meaningful insights, as it helps prioritize information that is critical for decision-making.
-
Audit and Monitoring Tools: Implement tools capable of providing audit trails and monitoring capabilities. These tools will track access and modifications to sensitive objects, ensuring compliance with security policies and enabling swift responses to any irregularities. By utilizing these technologies, organizations can enhance their information governance practices and support informed decision-making.
In comparing RLS and OLS, it is important to note that while RLS uses DAX filters to restrict the display of information, OLS employs object level security by completely removing restricted objects from the semantic model for unauthorized users. This key difference can lead to potential confusion if users encounter errors when accessing reports that reference hidden measures.
By proactively addressing these prerequisites, organizations can significantly enhance the effectiveness of their object level security implementation, ultimately leading to a more secure environment for managing sensitive information and fostering operational efficiency through advanced technology solutions. Moreover, integrating RPA can specifically help alleviate manual tasks associated with OLS implementation, further streamlining processes and enhancing overall productivity.
Step-by-Step Guide to Implementing Object Level Security
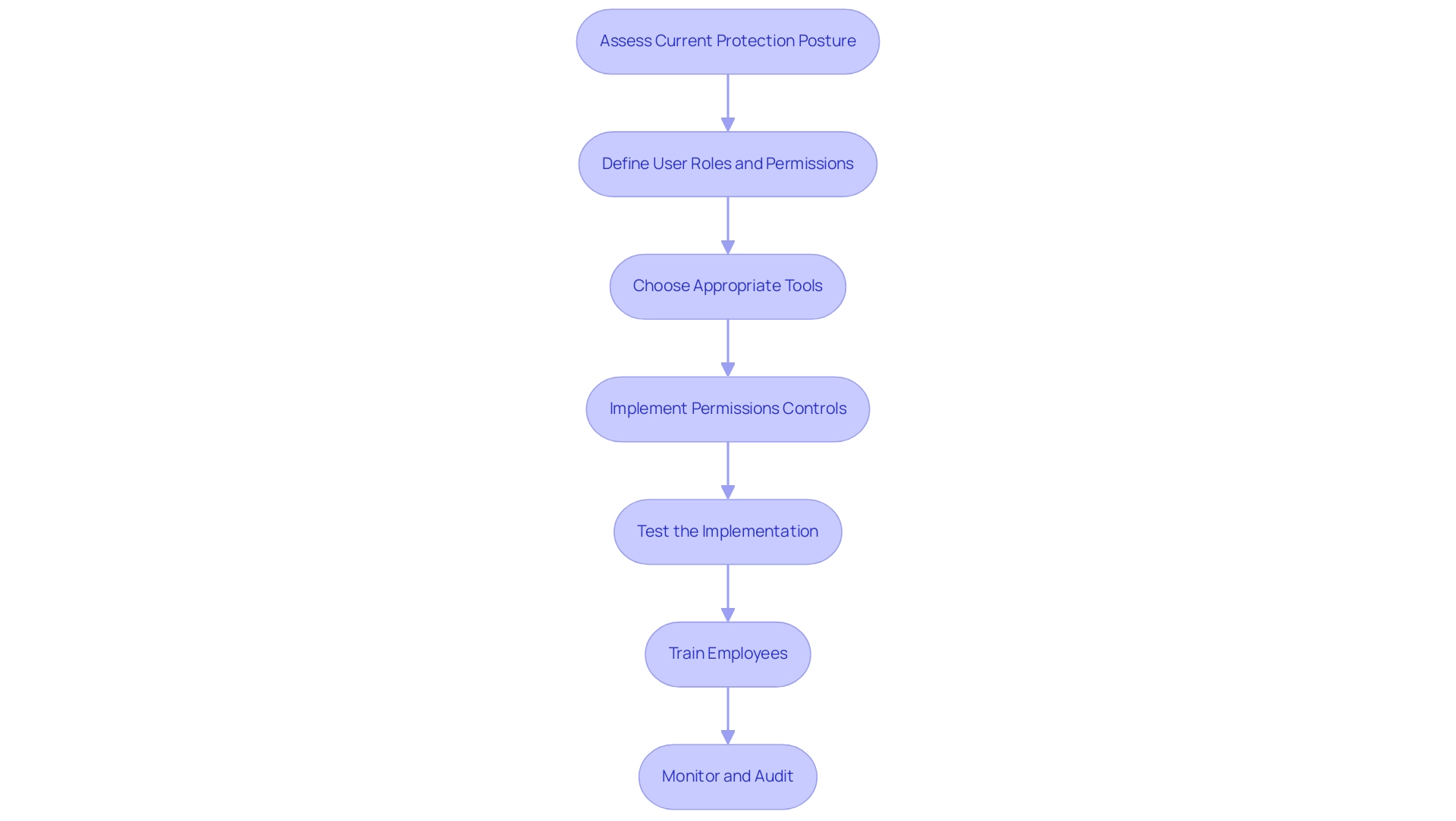
Implementing object level security in Power BI is essential for safeguarding sensitive customer information and enhancing operational efficiency through insights based on information. Here is a step-by-step guide to effectively set up OLS:
-
Assess Current Protection Posture:
Begin by evaluating your existing measures to identify gaps where OLS can enhance defense.
This foundational understanding will help overcome challenges like data inconsistencies that can hinder actionable insights. -
Define User Roles and Permissions:
Engage with stakeholders across departments to establish clear user roles and the specific permissions necessary for each role.
This collaborative approach ensures that all critical perspectives are considered, fostering a culture of security awareness that aligns with the principles of Business Intelligence. -
Choose Appropriate Tools:
Select the right control software and monitoring tools tailored to your organization’s unique needs.
The choice between free and paid versions, such as Tabular Editor 2 and Tabular Editor 3, should be made based on the complexity of your models and required features.
Tabular Editor 2 offers basic functionalities suitable for simpler models, while Tabular Editor 3 provides advanced features for more complex scenarios.
As Balivada Ganesh Bhargav notes,Tabular Editor is a widely used model metadata editor that provides a simple GUI for editing the Model Metadata instead of making changes in the script.
-
Implement Permissions Controls:
Configure the chosen software to enforce permissions controls based on the defined user roles.
Ensuring that these controls are correctly aligned with organizational requirements is crucial for effective data governance and can streamline the report creation process in Power BI. -
Test the Implementation:
Conduct comprehensive testing to verify that control measures operate as intended and confirm that users can reach only the objects for which they are authorized.
This step is vital to ensure the integrity of your protection framework and to maintain the reliability of data-driven insights. -
Train Employees:
Provide thorough training for employees on the new access protocols and the significance of OLS.
Training your team promotes a culture of awareness and compliance, which is crucial considering that organizations implementing object level security have reported success rates of over 80% in improving data protection.
Furthermore, by automating protective processes through OLS, employees can concentrate on more strategic tasks, enhancing overall morale and productivity. -
Monitor and Audit:
Establish a routine for monitoring and auditing access logs to ensure compliance and quickly identify any unauthorized access attempts.
Routine evaluations assist in upholding an efficient defense stance and improving the trustworthiness of insights obtained from Power BI dashboards.
By adhering to these steps, organizations can effectively implement object level security, which greatly strengthens their information safeguarding measures and ensures adherence to privacy regulations.
It’s important to note that while Row Level Security (RLS) and OLS can be validated separately in Power BI, understanding their relationship and limitations is crucial for effective information management.
The combination of RLS and OLS highlights the significance of a layered protection approach for sensitive data management.
Moreover, utilizing Robotic Process Automation (RPA) alongside OLS can additionally streamline processes, minimizing manual efforts and improving operational efficiency.
Overcoming Challenges: Common Pitfalls in OLS Implementation
Implementing object level security presents various challenges that organizations must navigate to ensure successful deployment. The following are common pitfalls along with strategies to overcome them:
-
Resistance to Change: Employee resistance can significantly hinder the adoption of new control measures. Research indicates that this resistance is a prevalent issue, with a considerable percentage of employees expressing concerns over new protective measures. To mitigate this, involving employees early in the process and clearly communicating the benefits of object level security can foster a sense of ownership and acceptance.
-
Over-Complication of Roles: Creating overly complex user roles can lead to confusion and inefficiencies in management. Experts suggest simplifying roles whenever feasible to enable smoother operations and clearer comprehension of privileges.
-
Neglecting Regular Audits: Without regular audits, organizations may unintentionally leave gaps that can be exploited. It is essential to schedule periodic reviews of access logs and permissions to uphold the integrity of protective measures. This practice not only fortifies defenses but also aligns with best practices in cybersecurity. Notably, statistics show that only 1 in 4 companies were able to thwart ransomware attacks before their data was fully encrypted, highlighting the critical need for robust protective measures.
-
Inadequate Training: Comprehensive training on new policies and procedures related to object level security is crucial for fostering compliance and understanding among employees. Ensuring that all staff members are well-informed can significantly reduce resistance and enhance the overall stance.
By being proactive in addressing these challenges, organizations can significantly improve the success of their object level security implementation. The development of advanced systems like DetectorGuard demonstrates how focusing on localized features and removing adversarial patches can enhance detection performance. As Liang et al. emphasize, there is potential to significantly improve the performance of mainstream object detection systems by extending the width and depth of the backbone network. Furthermore, the expansion of application scope through the fusion of multi-dimensional targets showcases real-world applications of object level security, which enhances adaptability and robustness in protective measures.
Best Practices for Maintaining Object Level Security
To effectively maintain Object Level Security (OLS), organizations should adhere to the following best practices:
-
Regularly Review Access Permissions: Conduct periodic assessments of user roles and permissions to ensure they are aligned with current job functions and responsibilities. This proactive strategy not only assists in reducing unauthorized entry but also improves overall safety effectiveness. Routine evaluations are crucial in spotting and correcting inconsistencies, which is essential for maintaining object level security to protect sensitive information. Data protection is designed to mitigate the threat of unauthorized data access, emphasizing the importance of these reviews.
-
Update Security Policies: Security policies should be revised regularly to accommodate changes in regulations, technology, and organizational structure. Updating these policies is critical, as highlighted by experts who stress the need for agility in response to evolving threats. A well-organized policy framework guarantees that protective measures remain strong and effective. As noted, a bucket policy that allows a wildcard action “*” can potentially allow a user to perform any action in the bucket, underscoring the risks associated with inadequate policy updates.
-
Conduct Training Refreshers: Ongoing training sessions are essential for keeping employees informed about best practices and updates related to object level security. Regular refreshers ensure that staff are aware of their roles in maintaining safety and can promptly act in accordance with established protocols.
-
Utilize Automation: The integration of Robotic Process Automation (RPA) tools can significantly streamline the monitoring of access logs and alerts for unauthorized access attempts. Recent advancements in automation not only enhance efficiency but also improve the precision of monitoring, allowing organizations to respond swiftly to potential threats. Organizations are increasingly adopting automated systems not only to strengthen their protective measures but also to reduce the burden on IT teams and enhance overall productivity. Additionally, implementing RPA can lead to cost savings by minimizing manual interventions and optimizing resource allocation.
-
Implement Incident Response Plans: A clear incident response plan is vital for preparing for potential breaches. This plan should outline specific steps for containment and recovery, ensuring that organizations can respond effectively to incidents. As highlighted in the case study on Access Control Entries (ACE), managing ACEs defines specific permissions for users, including view, read, create, write, execute, delete, permission change, and ownership. By managing ACEs, administrators can refine user permissions and control over objects, improving the overall safety of the system. Thus, having a robust incident response framework is crucial for mitigating risks associated with such policies.
-
Leverage Business Intelligence: Utilizing Business Intelligence tools can transform raw information into actionable insights, enabling organizations to make informed choices regarding their protection practices. By analyzing access patterns and identifying anomalies, businesses can proactively address potential vulnerabilities.
By following these best practices, organizations can ensure that their object level security measures remain effective and responsive to evolving threats, ultimately enhancing their data security landscape while leveraging RPA, tailored AI solutions, and Business Intelligence for informed decision-making.
Conclusion
Implementing Object Level Security (OLS) is not just a strategic advantage; it is a fundamental necessity for organizations operating in today’s complex digital landscape. By understanding and applying key concepts such as:
- Granular access control
- Role-based access control
- The importance of audit trails
organizations can significantly enhance their security posture. These measures are essential in mitigating risks associated with data breaches and ensuring compliance with stringent regulations.
Moreover, the integration of OLS not only protects sensitive data but also fosters operational efficiency, allowing employees to perform their roles effectively without unnecessary barriers. As organizations embrace technologies like Robotic Process Automation and Business Intelligence, the synergy between these tools and OLS becomes increasingly vital, transforming security into a facilitator of informed decision-making.
As organizations prepare to implement OLS, it is crucial to focus on best practices such as:
- Regular access reviews
- Ongoing training
- The utilization of automation to streamline security processes
By proactively addressing common challenges and continuously refining security measures, organizations can safeguard their data integrity and foster a culture of compliance.
In conclusion, the proactive adoption of Object Level Security is an indispensable aspect of a robust data protection strategy. It is a vital investment in both security and operational efficiency, empowering organizations to navigate the evolving cyber threat landscape with confidence and resilience.

